简介
主要介绍下linux下emmc(延伸到块设备)信息的获取
/proc/partition接口
这是我们的板子显示的内容,这里的block的单位是KB,一开始我以为是512byte
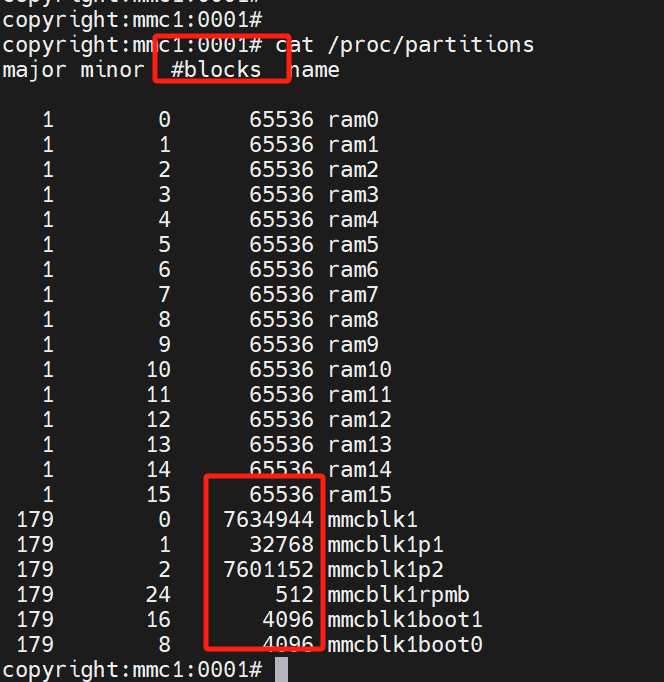
对比这里的大小信息可以跟上面的信息对应
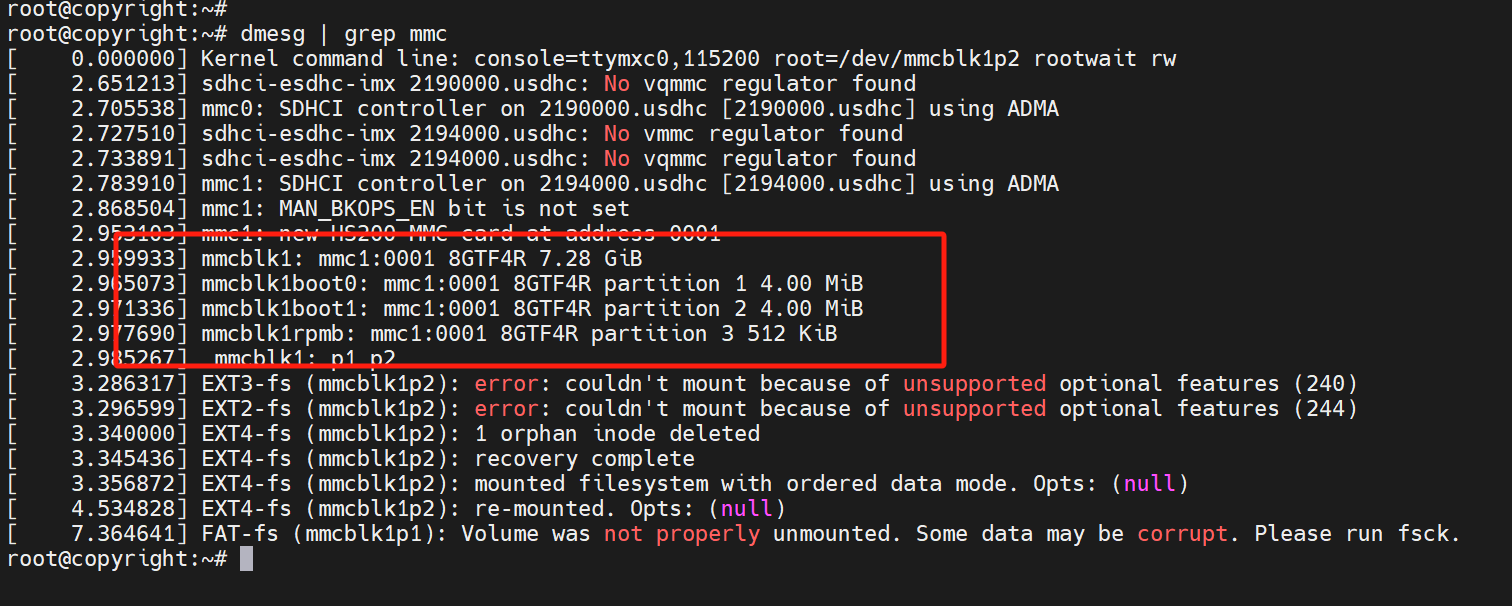
如果是cmdline传参,给分区设置名字的话,还会显示
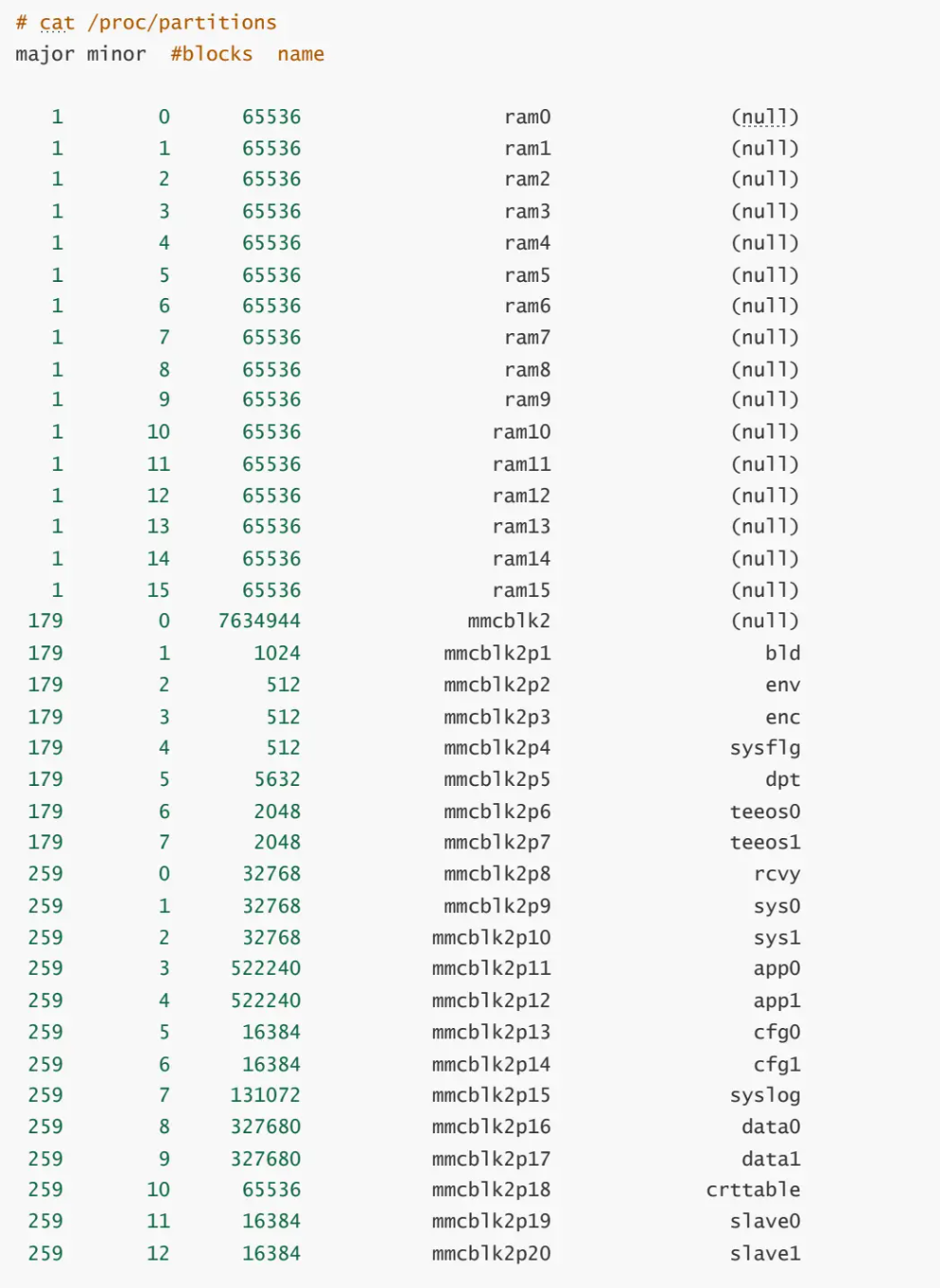
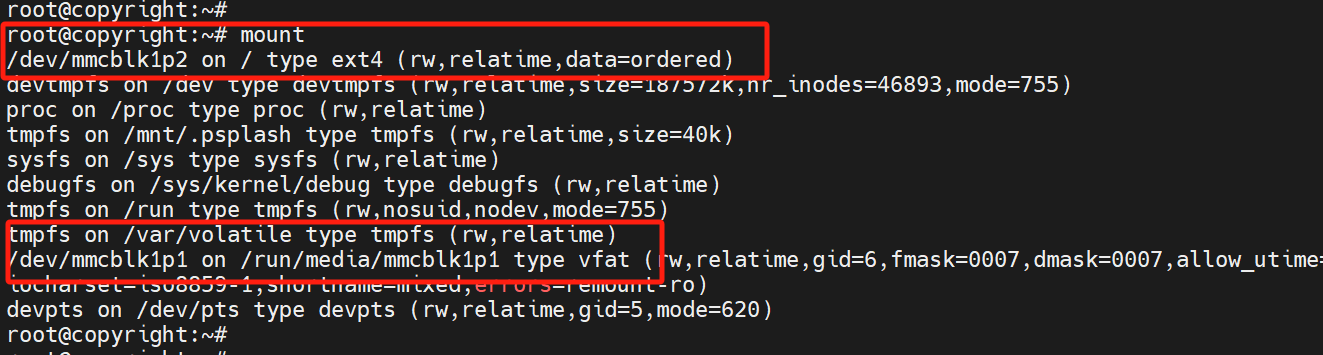
mount查看分区挂载情况
执行mount命令,可以查看分区挂载的情况。
fdisk -l
输入fdisk -l这个命令
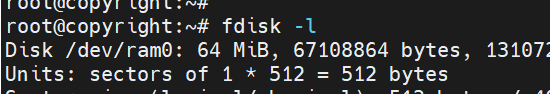
可以看到能显示具体的type
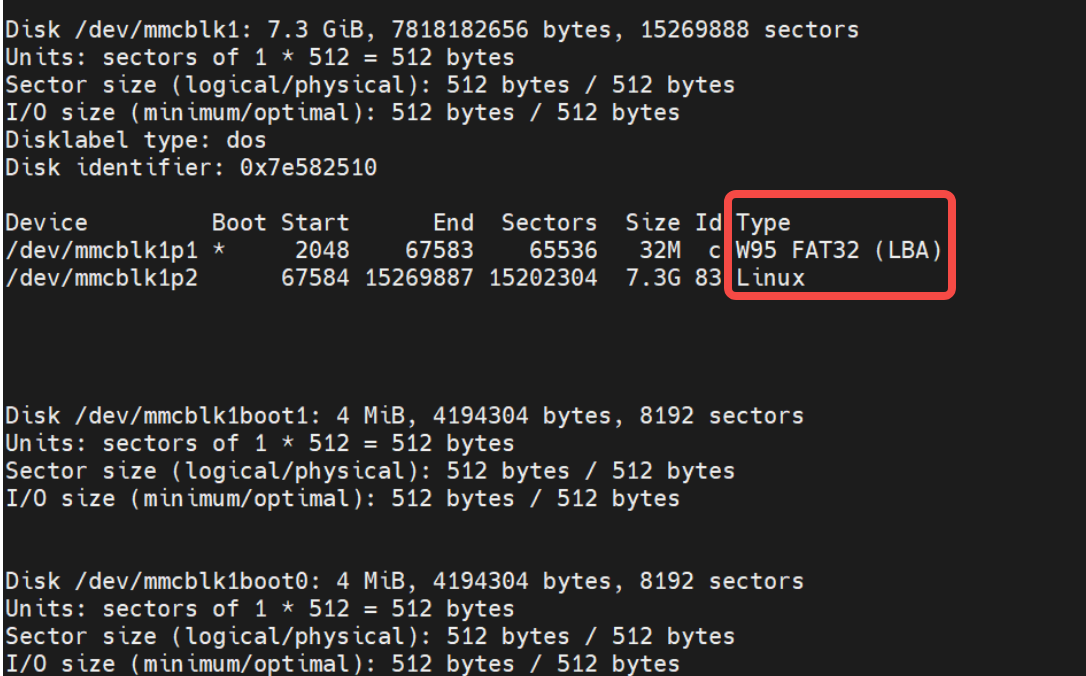
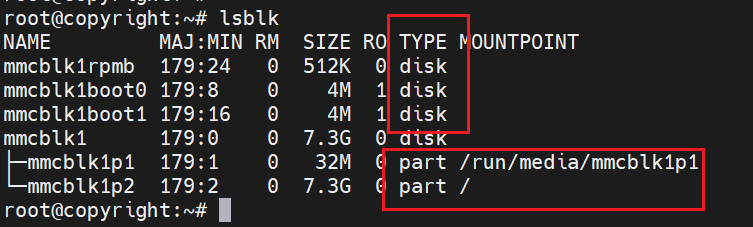
lsblk
lsblk命令的输出可以看到boot ,rpmb, uda分区都是 type disk的,而uda里面各自的分区显示的是part,这个其实跟内核块设备驱动中的mmc_add_disk跟mmc_blk_alloc_part相关,后面会分析到的
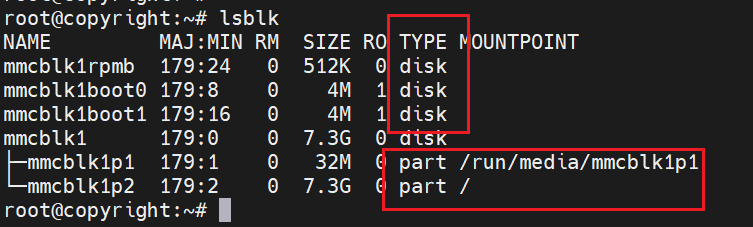
/sys/class/block 查看eMMC分区情况
在 /sys/class/block/ 目录下可以查看当前系统的分区情况:
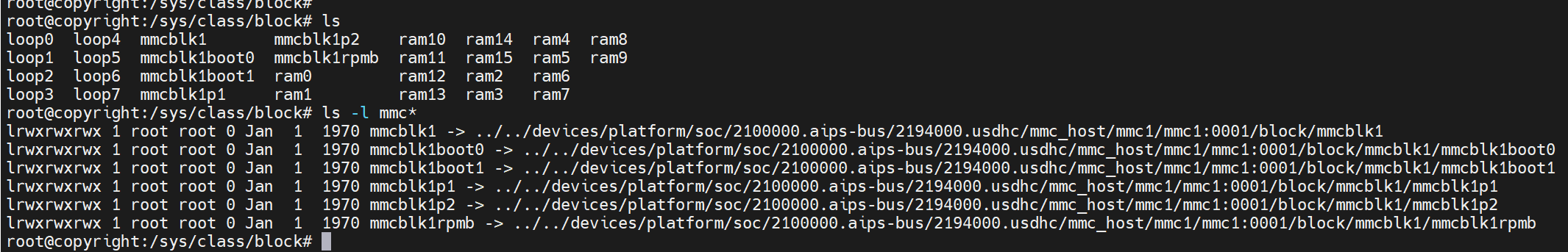
root@copyright:/sys/class/block# ls
loop0 loop4 mmcblk1 mmcblk1p2 ram10 ram14 ram4 ram8
loop1 loop5 mmcblk1boot0 mmcblk1rpmb ram11 ram15 ram5 ram9
loop2 loop6 mmcblk1boot1 ram0 ram12 ram2 ram6
loop3 loop7 mmcblk1p1 ram1 ram13 ram3 ram7
root@copyright:/sys/class/block# ls -l mmc*
lrwxrwxrwx 1 root root 0 Jan 1 1970 mmcblk1 -> ../../devices/platform/soc/2100000.aips-bus/2194000.usdhc/mmc_host/mmc1/mmc1:0001/block/mmcblk1
lrwxrwxrwx 1 root root 0 Jan 1 1970 mmcblk1boot0 -> ../../devices/platform/soc/2100000.aips-bus/2194000.usdhc/mmc_host/mmc1/mmc1:0001/block/mmcblk1/mmcblk1boot0
lrwxrwxrwx 1 root root 0 Jan 1 1970 mmcblk1boot1 -> ../../devices/platform/soc/2100000.aips-bus/2194000.usdhc/mmc_host/mmc1/mmc1:0001/block/mmcblk1/mmcblk1boot1
lrwxrwxrwx 1 root root 0 Jan 1 1970 mmcblk1p1 -> ../../devices/platform/soc/2100000.aips-bus/2194000.usdhc/mmc_host/mmc1/mmc1:0001/block/mmcblk1/mmcblk1p1
lrwxrwxrwx 1 root root 0 Jan 1 1970 mmcblk1p2 -> ../../devices/platform/soc/2100000.aips-bus/2194000.usdhc/mmc_host/mmc1/mmc1:0001/block/mmcblk1/mmcblk1p2
lrwxrwxrwx 1 root root 0 Jan 1 1970 mmcblk1rpmb -> ../../devices/platform/soc/2100000.aips-bus/2194000.usdhc/mmc_host/mmc1/mmc1:0001/block/mmcblk1/mmcblk1rpmb
root@copyright:/sys/class/block#
从上面的信息可以知道:
- 这个
eMMC上总共共有5个分区,boot0/boot1/rpmb/p1/p2分区; - 这个
eMMC用到的控制器为2194000.usdhc; - 我们可以到软连接显示的
../../devices/platform/soc/2100000.aips-bus/2194000.usdhc/mmc_host/mmc1/mmc1:0001/block/mmcblk1/目录下查看更具体的信息;
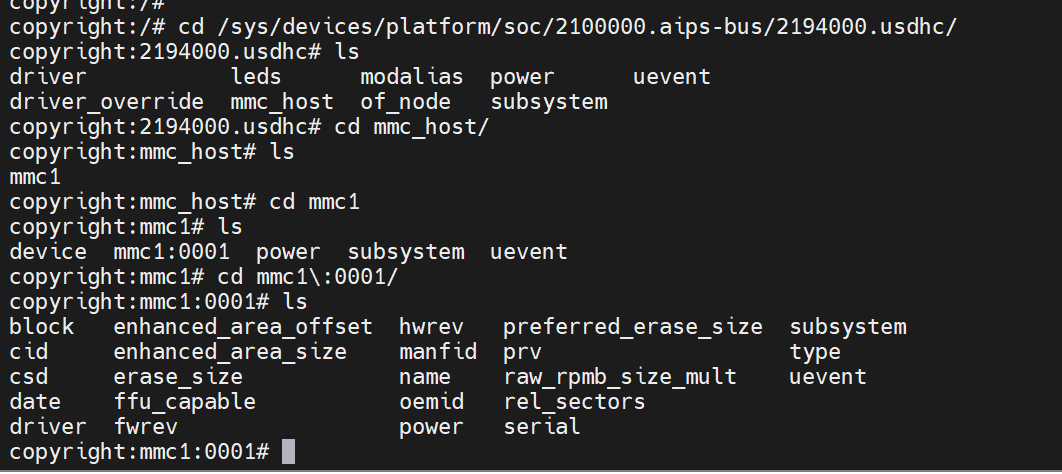
目录下还有我们boot,rpmb,uda分区的信息
关于这些参数的意义,可以参考如下两个链接
https://www.kernel.org/doc/Documentation/ABI/testing/sysfs-block
https://www.kernel.org/doc/Documentation/block/stat.txt
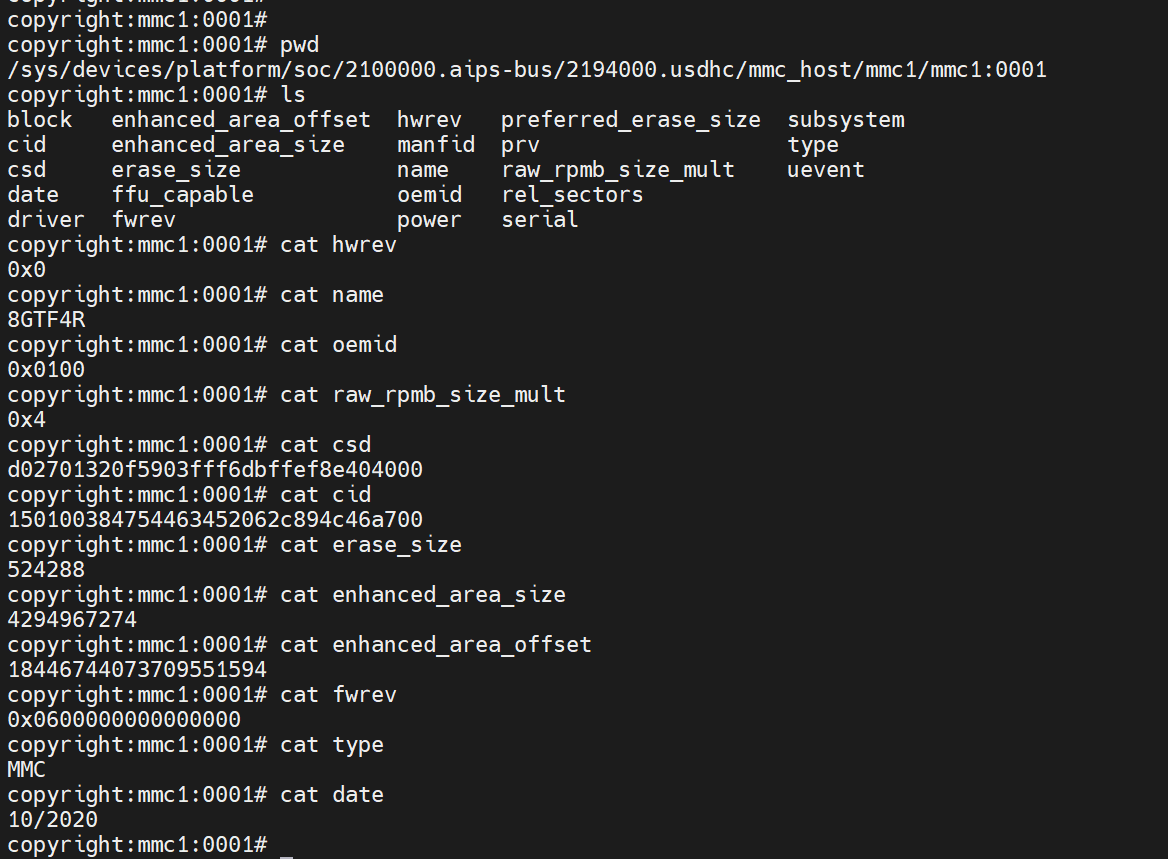
这里简单的现实下几个特性,这里的mmc1:0001表示mmc1控制器,rca地址为0001的emmc卡
下面看了hwrev,name,oemid,raw_rpmb_size_mult,csd,cid,erase_size,enhanced_area_size,enhanced_area_offset,fwrev,type,date
查看各个分区的大小
两种方法,一种是fdisk/lsblk,一种是sysfs
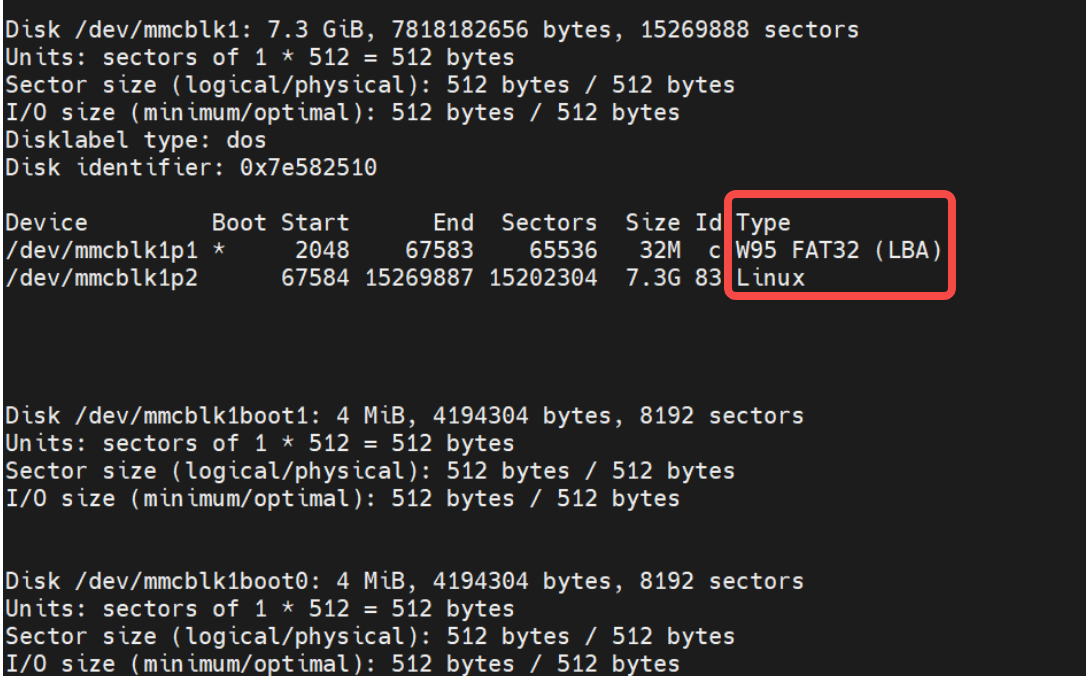
fdisk / lsblk
fdisk显示了start,end,sector
sysfs
另一种是sysfs的方法
uda分区
在/sys/devices/platform/soc/2100000.aips-bus/2194000.usdhc/mmc_host/mmc1/mmc1:0001/block目录下,有几个以mmcblk1开头的目录名,这里面包含了分区的起始和block的块数
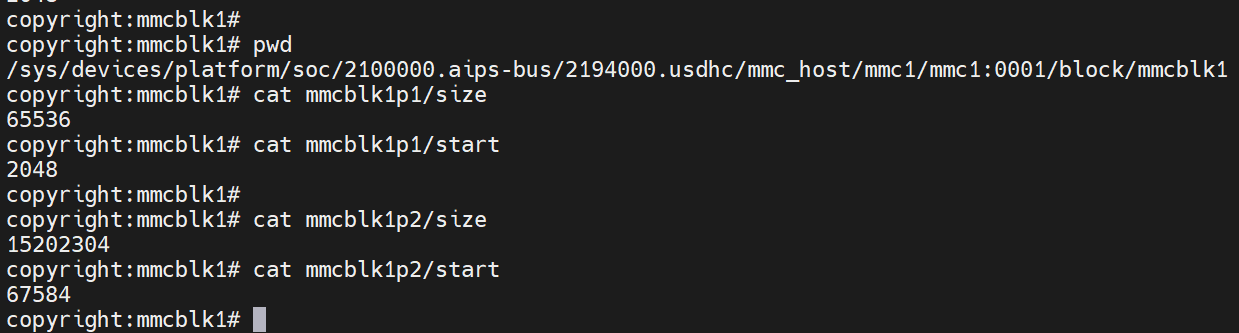
- 以
mmcblk1p1为例,这里的start单位是block,也就是第2048块,size是65536,也就是p1分区大小为65536*512byte=32MB - 以
mmcblk1p2为例,这里的start单位是block,也就是第67584块,size是15202304,也就是p2分区大小为15202304*512byte=7423MB
跟前面fdsik /lsblk 显示的信息是一样的,且这里可以看到p1开始前面有部分区域是空的,放了个分区表(注意分区管理只针对uda分区)
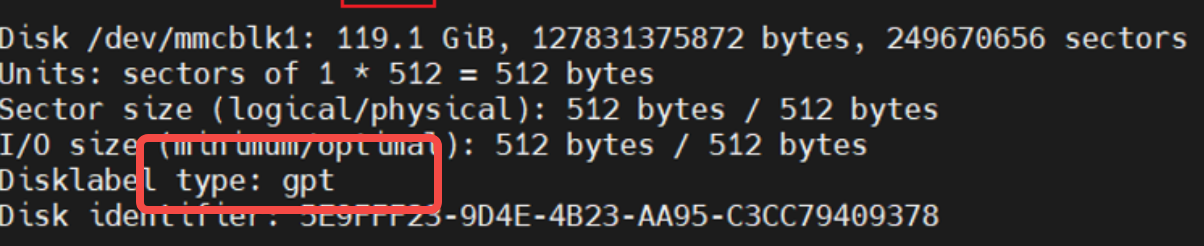
像如果是gpt分区的话,fdisk中的disklabel type会显示gpt
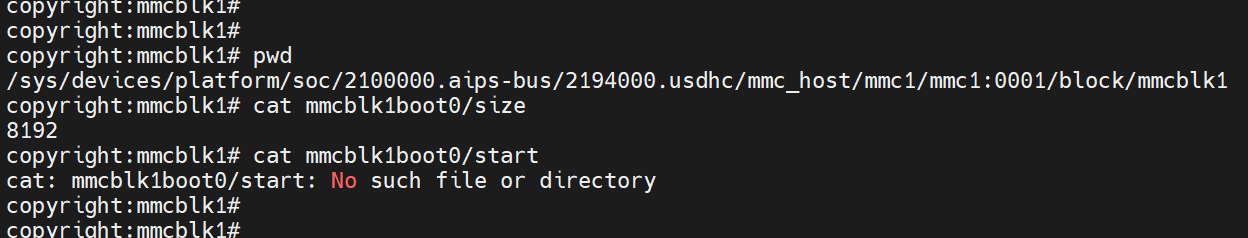
boot分区
没有start,只有size
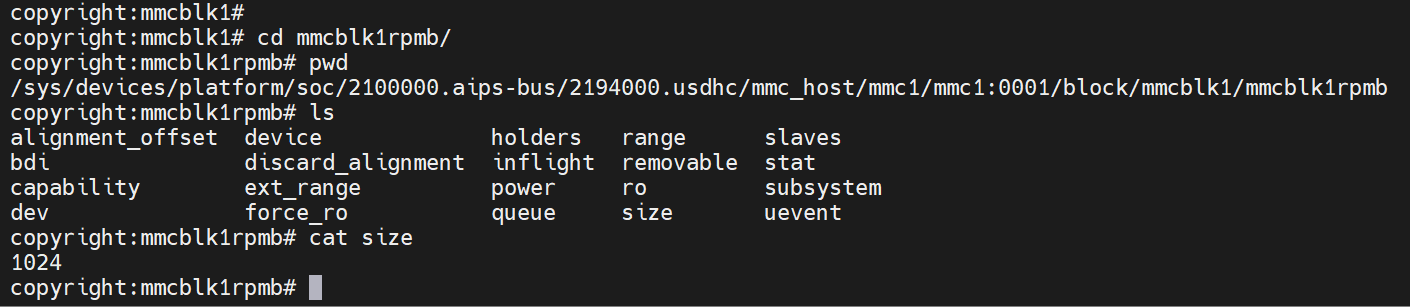
rpmb分区
一样
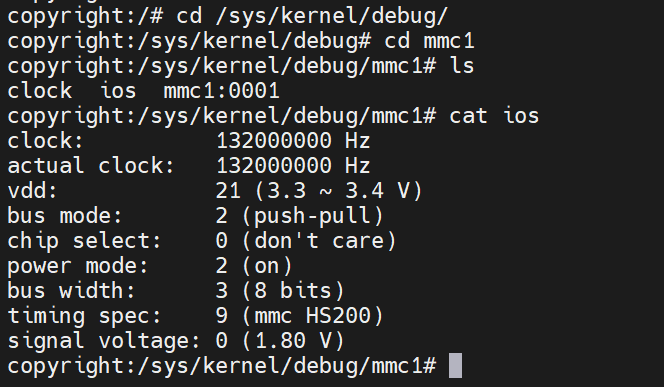
读取emmc控制器
首先执行:mount -t debugfs none /sys/kernel/debug/, 在/sys/kernel/debug/mmc1目录下,cat ios可以查看这个eMMC控制器的工作频率和位宽基本信息。
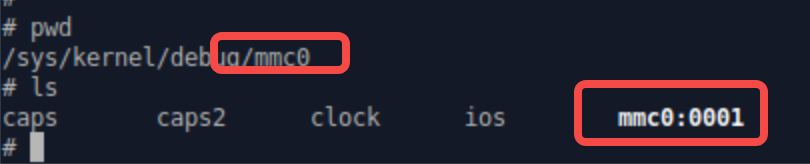
像这里的mmc0是控制器的信息,而不是外接的emmc卡信息哦,emmc卡信息是mmc0:0001这种带地址的,这里也是有个host,device的思想
读取ext_csd寄存器
这个寄存器属于csd扩展出来的,需要将debugfs挂载出来才能读取到。注意这里读的是emmc卡的信息,相当于device了。
在/sys/kernel/debug/mmc1/mmc1\:0001/目录下就可以看到ext_csd寄存器了。cat ext_csd可以得到一个512字节大小的数据,如下
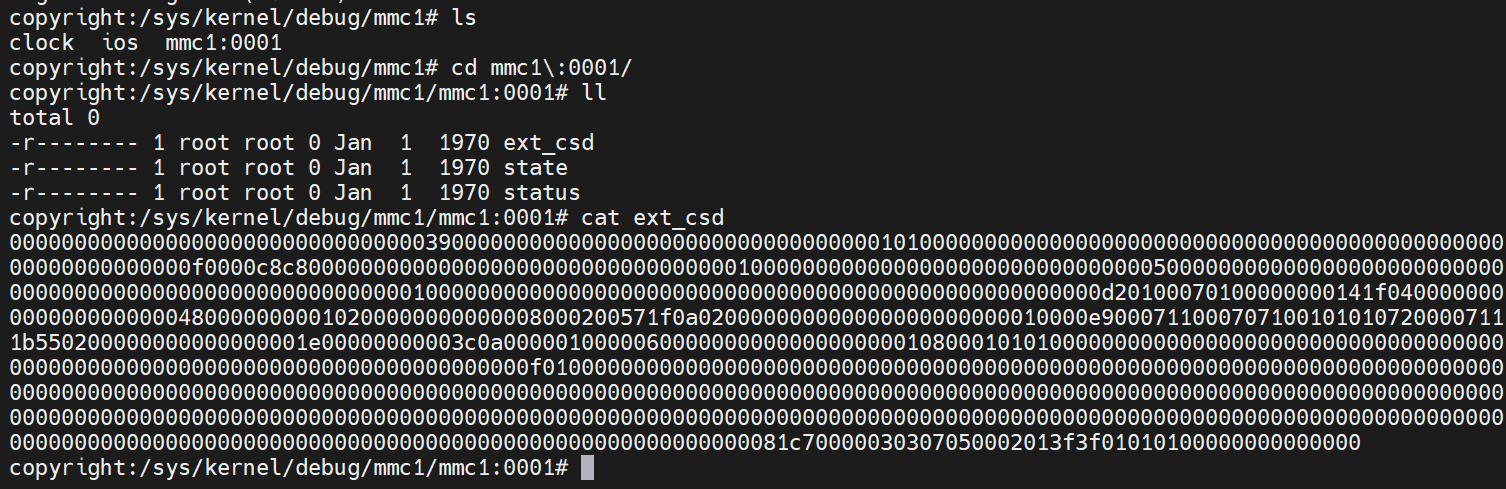
当然这样看很难看,无法很快的确认寄存器中某些位的值。因此,网上就有个小哥写了个python脚本来解析这512字节的数据,以常人可以理解的格式进行解析。详见此链接
脚本这里就先贴出来,其中的ecsd_str字符串要换成我们图片上的这些字符串
#!/usr/bin/env python
"""
Author: Kyle Manna <kyle@kylemanna.com>
Blog: https://blog.kylemanna.com
"""
import binascii
import re
import sys
def str2bytearray(s):
if len(s) % 2:
s = '0' + s
reorder = True
if reorder:
r = []
i = 1
while i <= len(s):
r.append(s[len(s) - i - 1])
r.append(s[len(s) - i])
i += 2
s = ''.join(r)
out = binascii.unhexlify(s)
return out
if __name__ == '__main__':
ecsd_str = '000000000000000000000000000000003900000000000000000000000000000000010100000000000000000000000000000000000000000000000000000000000f0000c8c800000000000000000000000000000000010000000000000000000000000000000500000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000d20100070100000000141f04000000000000000000004800000000010200000000000008000200571f0a020000000000000000000000010000e90007110007071001010107200007111b550200000000000000001e00000000003c0a000001000006000000000000000000010800010101000000000000000000000000000000000000000000000000000000000000000000000000000f0100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000081c70000030307050002013f3f01010100000000000000'
#ecsd_str = '320100'
ecsd = str2bytearray(ecsd_str)
csd_len = len(ecsd)
line_len = 16
i = 0
while i < len(ecsd):
sys.stdout.write("{0:04d}:\t".format(i))
for j in range(line_len):
if (i < csd_len):
sys.stdout.write("{0:=02x}".format(ord(ecsd[csd_len-i-1])))
i = i + 1
else:
break
if (j == (line_len - 1)): pass
elif (i % 4): sys.stdout.write(" ")
else: sys.stdout.write(" ")
sys.stdout.write("\n")
print "BOOT_SIZE_MULTI[226] = 0x{:x}".format(ord(ecsd[csd_len-168-1]))
复制然后放到我们板子执行
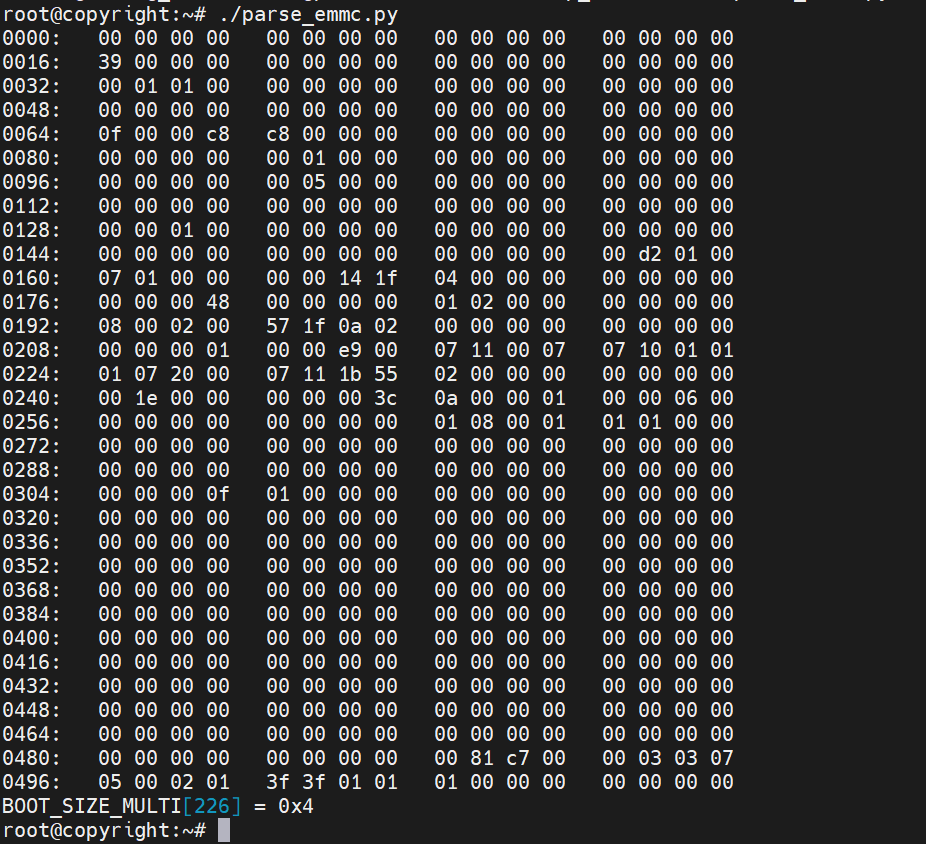
这里解析了很多信息出来,结合spec可以更仔细的看
root@copyright:~# ./parse_emmc.py
0000: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0016: 39 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0032: 00 01 01 00 00 00 00 00 00 00 00 00 00 00 00 00
0048: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0064: 0f 00 00 c8 c8 00 00 00 00 00 00 00 00 00 00 00
0080: 00 00 00 00 00 01 00 00 00 00 00 00 00 00 00 00
0096: 00 00 00 00 00 05 00 00 00 00 00 00 00 00 00 00
0112: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0128: 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00
0144: 00 00 00 00 00 00 00 00 00 00 00 00 00 d2 01 00
0160: 07 01 00 00 00 00 14 1f 04 00 00 00 00 00 00 00
0176: 00 00 00 48 00 00 00 00 01 02 00 00 00 00 00 00
0192: 08 00 02 00 57 1f 0a 02 00 00 00 00 00 00 00 00
0208: 00 00 00 01 00 00 e9 00 07 11 00 07 07 10 01 01
0224: 01 07 20 00 07 11 1b 55 02 00 00 00 00 00 00 00
0240: 00 1e 00 00 00 00 00 3c 0a 00 00 01 00 00 06 00
0256: 00 00 00 00 00 00 00 00 01 08 00 01 01 01 00 00
0272: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0288: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0304: 00 00 00 0f 01 00 00 00 00 00 00 00 00 00 00 00
0320: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0336: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0352: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0368: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0384: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0400: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0416: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0432: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0448: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0464: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0480: 00 00 00 00 00 00 00 00 00 81 c7 00 00 03 03 07
0496: 05 00 02 01 3f 3f 01 01 01 00 00 00 00 00 00 00
BOOT_SIZE_MULTI[226] = 0x4
root@copyright:~#
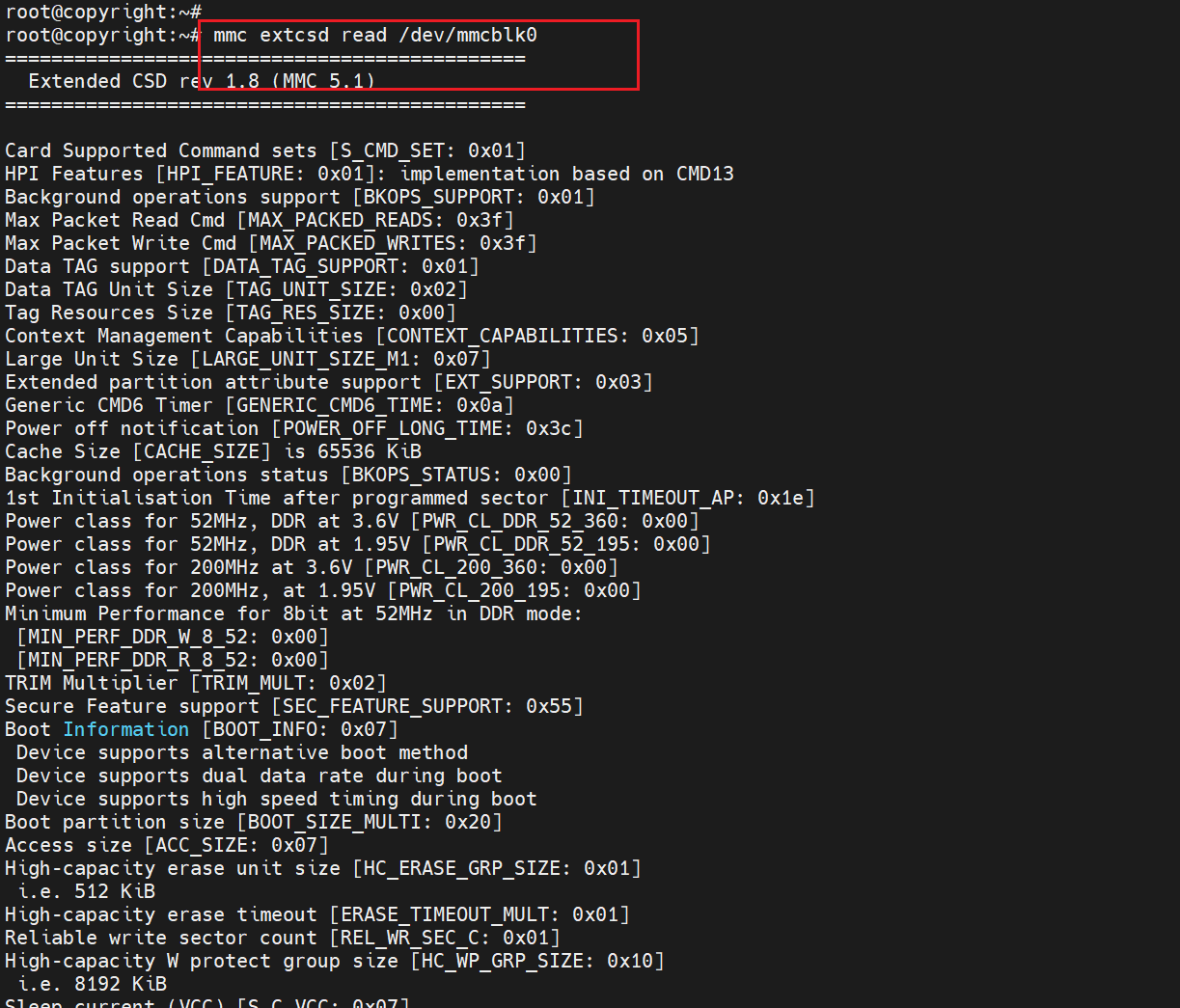
mmc工具
获取extcsd的信息
mmc extcsd read /dev/mmcblk0
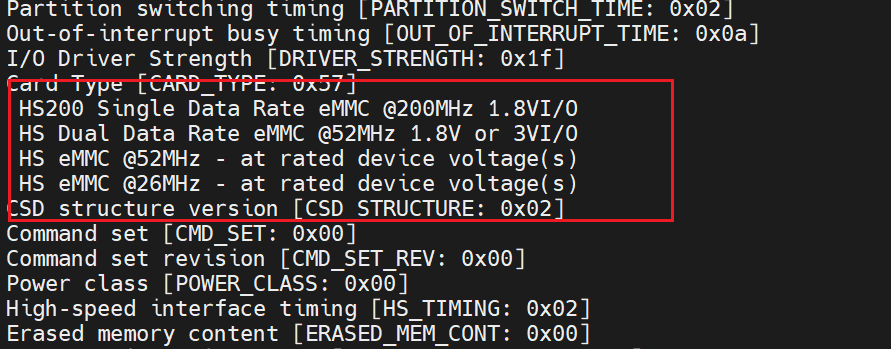
检查enhance的最大大小
mmc extcsd read /dev/mmcblk0 | grep MAX_ENH_SIZE_MULT -A 1
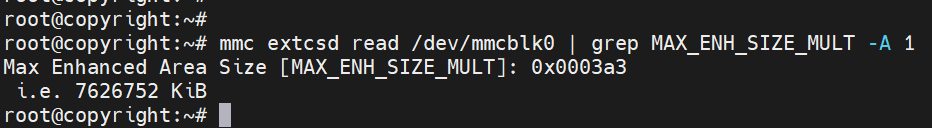
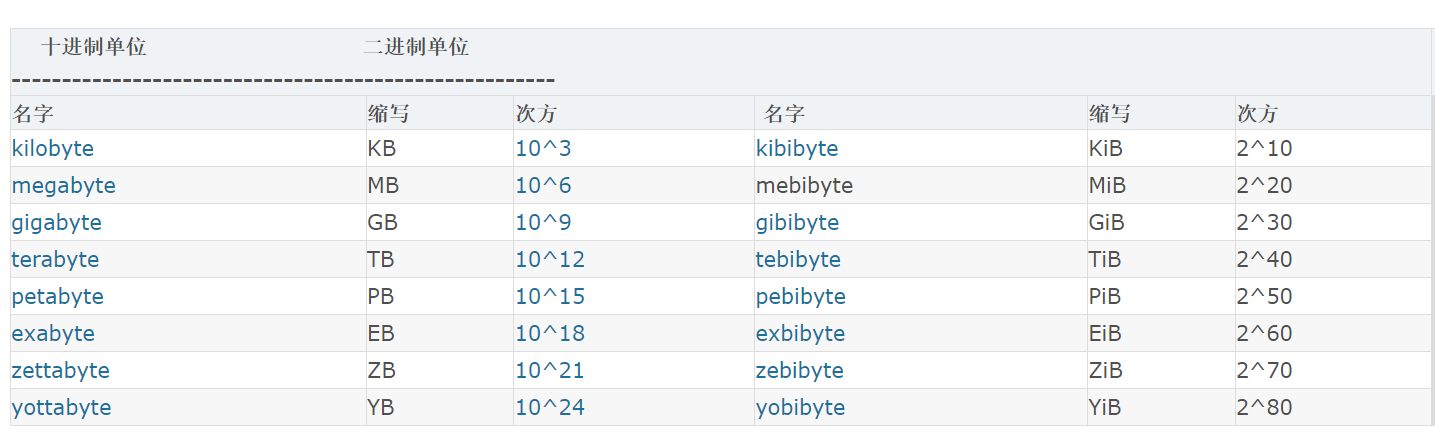
MiB跟MB的区别